Why Do Traditional Anonymization Methods Fail?
In today’s article, we will examine the anonymization of a petition created specifically for this analysis. We will use traditional methods commonly employed by workers in various organizations.
In the first case, we will anonymize the personal data of an official and the petitioner using an everyday office item—sticky notes. In the second case, we will obscure the official’s data with a pen and the petitioner’s data with a marker.
Then, we will use free online tools to apply simple filters to these documents, revealing the previously anonymized data.
Petition in Polish that we will anonymize manually today.
For the purposes of today’s article, we created a petition, which we then anonymized using traditional methods and subsequently scanned the redacted documents.

Sticky Notes and Markers: A False Sense of Security
Sticky notes and markers are commonly used in offices to conceal sensitive information in paper documents. While they may seem effective, they do not provide lasting data protection. They leave room for fragments of information to be recovered using appropriate techniques, such as image filtering.
Sticky Notes – When covering text with sticky notes, some fragments may still be visible without us realizing it. By using image processing tools, such as contrast adjustments, it is possible to restore the visibility of the covered information.

Markers and Correction Fluid – Markers and correction fluid do not always obscure text completely. Adjusting contrast, saturation, or brightness can reveal information that was meant to be anonymized.
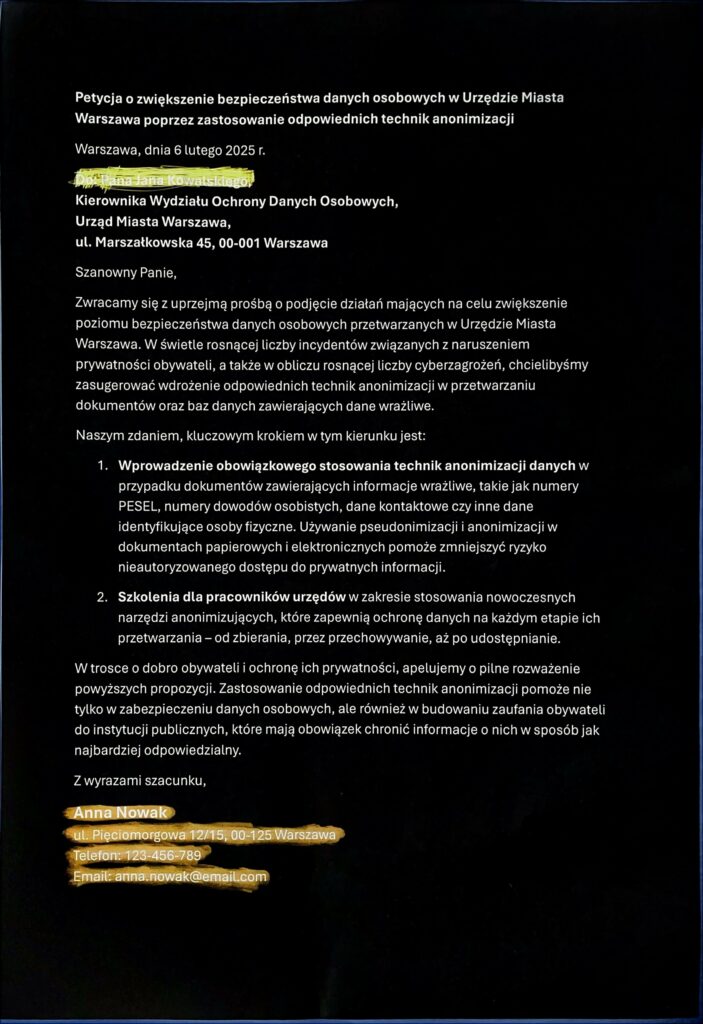
Consequences:
A document that appears to be anonymized may still contain accessible sensitive data, which can be recovered using digital techniques. Worse yet, many employees are unaware of this risk because they have used these methods for years without encountering problems. The routine practice of covering data with sticky notes, markers, or correction fluid becomes a habit, reinforcing the false belief that these methods are effective.
Overlooking small gaps, using a marker that isn’t thick enough, or leaving barely visible traces of correction fluid can make hidden information readable after image processing. A single mistake—a slightly misaligned cover-up or an unintended reflection of light on the document’s surface—can expose what was meant to remain hidden. As a result, sensitive data may be unintentionally disclosed, and the consequences of this error may only become apparent when it is too late to prevent a data breach.